Cloud demands cloud-native security
Finding & fixing cloud infra security issues at cloud speed
Cloud Platforms consist of hundreds of thousands of server hardware wrapped in layers of software. It may look like a regular Information Technology and Security problem to some.
Cloud Service Providers (CSPs) have worked hard to ensure we can use the same server operating systems on the cloud we are used to in our enterprises. Their marketing departments spend a lot of effort convincing us we can simply lift our software, applications, and workloads and shift them to their cloud. They invest heavily in hardware, data centers, security certifications, etc. So it is not a big surprise that smart, technically inclined teams are left scratching their heads on what went wrong when data breaches happen.
A common prevalent myth - the cloud is secure by default
Cloud platforms are a giant blob of interconnected modules of the software.
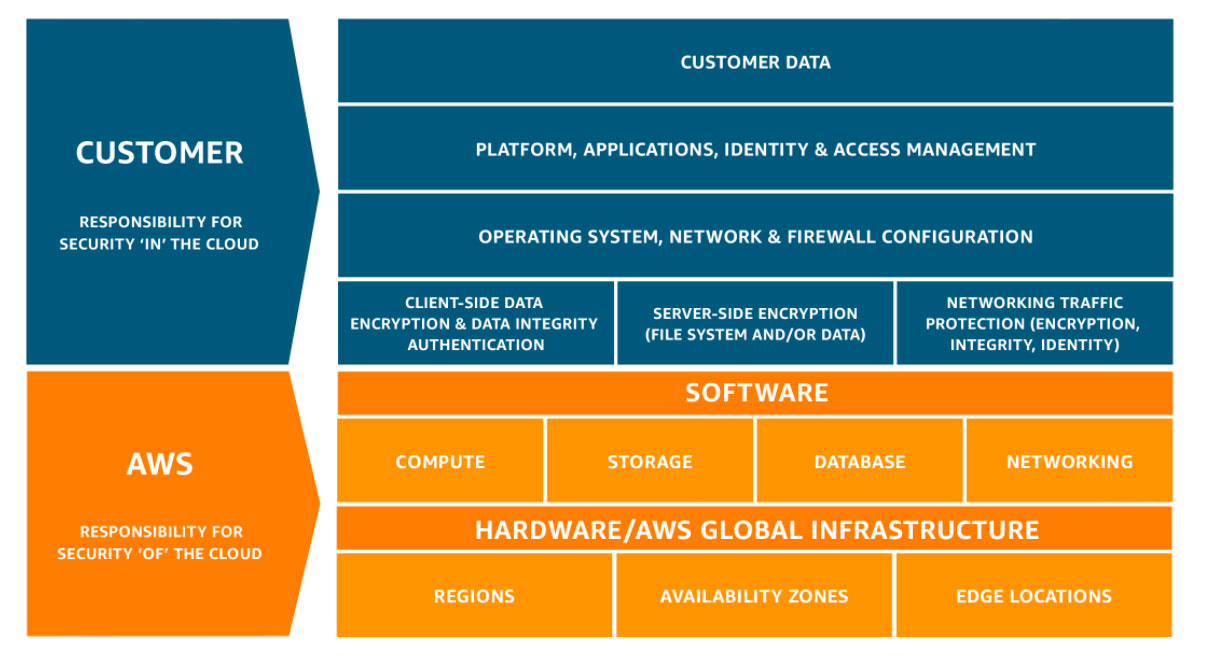
The myth prevails due to all the abstraction that creeps in when the hardware is virtualized when the network is defined as software (SDN). New words join the seemingly unremarkable words join lexicon like Virtual Private Cloud (VPC), and Shared Security Responsibility Model (SSRM).
SSRM is the get-out-of-jail card brandished by Cloud Service Providers whenever they release half-baked features with insecure defaults. Like any other software project with deadlines, sometimes bugs creep in. Sometimes features released are barebones. Other times the documentation isn’t complete. Even if all of this is taken care of, understanding the risk implications of choosing options is not an easy task.
The most significant implication of cloud platforms being software is that most configuration properties can be set and changed via APIs.
When one software property can make a private database public, the way to think about security monitoring can’t rely on monitoring the perimeter for attacks.
Thinking and acting like a cloud-native unlocks security for the cloud
Incredible possibilities open up when you can shed the old way of thinking and embrace the elastic nature of the public cloud. As a cloud-native, it would make sense to keep track of all configuration changes happening in real-time and take automated actions based on predetermined security policies.
To unlock cloud-native security, you need to do continuous visibility and evaluation. Once you have this in place, you can create security policies and even automatically enforce the policies using the same APIs of the cloud platforms.
Integrated Supply Chains on the public cloud have no option but to be cloud-native
With the complexity of modern businesses, with its interconnected supply chain, trying to secure without visibility and automated security process will not only be infeasible but leave you open to all kinds of opportunistic attackers.
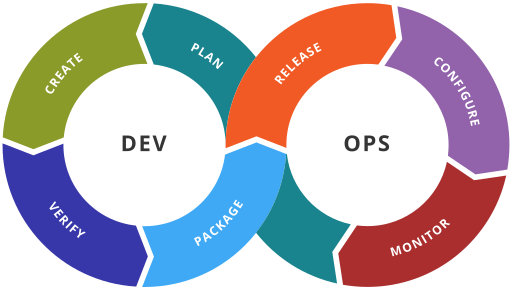
SREs understand and embrace the DevOps Loop
Planning leads to building leads to releasing leads to monitoring, and so on and so forth.
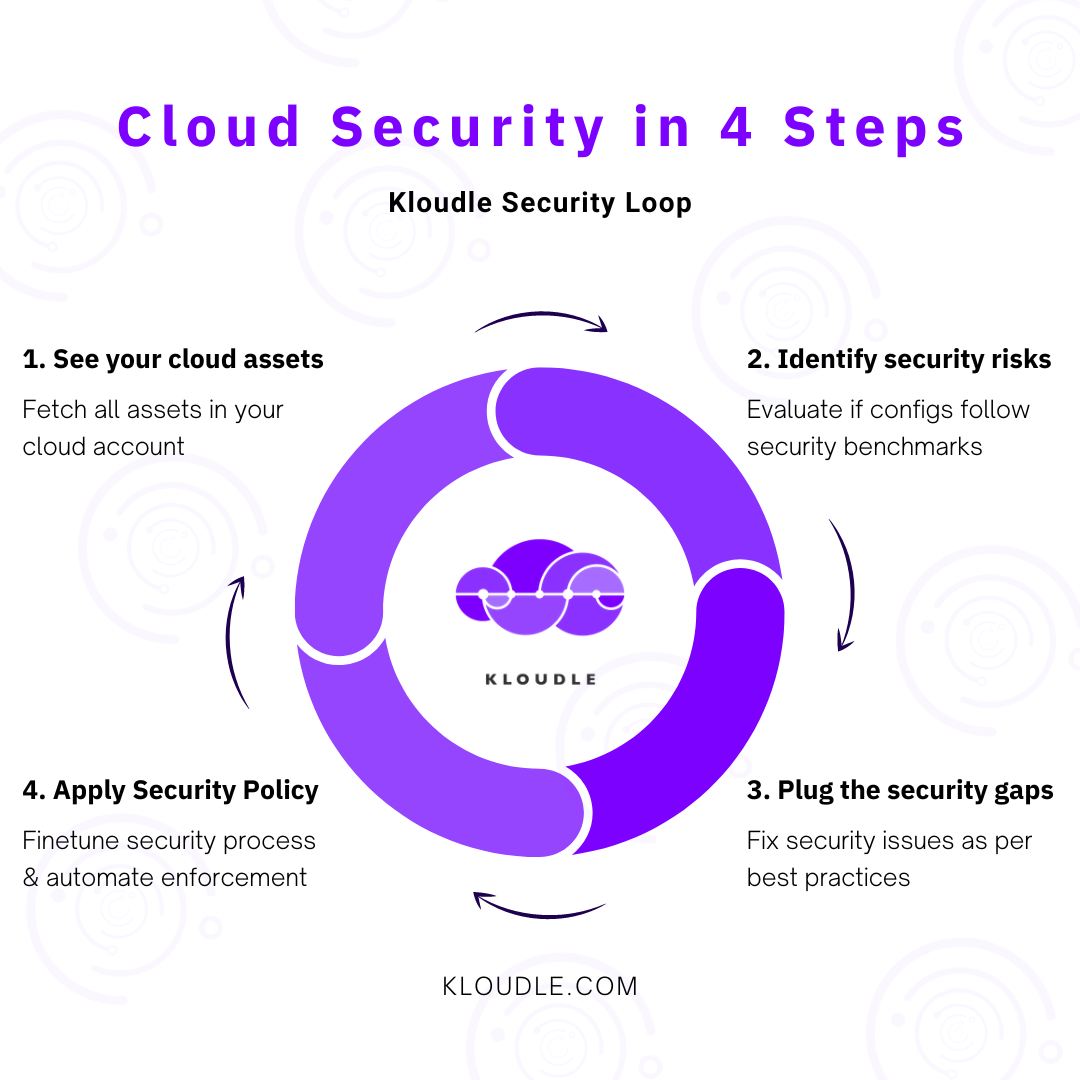
We built Kloudle around similar principles and concepts of a continuous security loop. It is great to start with visibility of assets, identify security risks, plug or accept security gaps, and tweak security processes. This needs to be repeated as long as we have infrastructure needing security in the cloud.
Cloud Security in 4 Steps using the Kloudle Security Loop
Kloudle automates the four steps required for cloud security in a loop. This allows us to eliminate toil stemming from security-related tasks SREs struggle with.
By embracing the Kloudle Security loop, all the DevOps teams need to focus on is finetuning the security policies and processes per their business needs.
At Kloudle, we have purpose-built a product for SREs and DevOps teams. Once you onboard your cloud account, you get an automatically refreshed updated inventory of cloud resources and every possible associated security misconfiguration they have. Additionally, you see compliance gaps that need to be plugged in in one glance. Did I mention that this is done automatically with up to six daily snapshots?
We are running a closed beta for eligible customers. Book a demo https://calendly.com/kloudle-akash if you want to automate your AWS/Google cloud security.